[Splunk] - Authentication Anomalies on Windows Hosts - The Classic Brute Force
Virtual machines to power on:
DC
LinuxA
Let's switch gears from certificate services and take a deeper dive into windows authentication events and look at an example of a classic brute force technique.
MITRE provides a great overview of the details of this technique: https://attack.mitre.org/techniques/T1110/
There are many flavors of brute force attacks, as they can target many services and systems. For our purposes, we will keep things really simple and use the Metasploit smb module to perform our brute force attacks.
Let's start by creating a file that contains some passwords that we want to try, we will be targetting the "Administrator" user in our lab. Open up nano or vi on your LinuxA machine and fill the file with the follwowing:
Pass1
Pass2
Pass3
Pass4
Pass5
Pass6
Pass7
Pass8
Pass9
Pass10We know these passwords don't work, so you can enter in any value you like here.

Then go ahead and start Metasploit: sudo msfconsole
Once Metasploit is started, enter in the following commands:
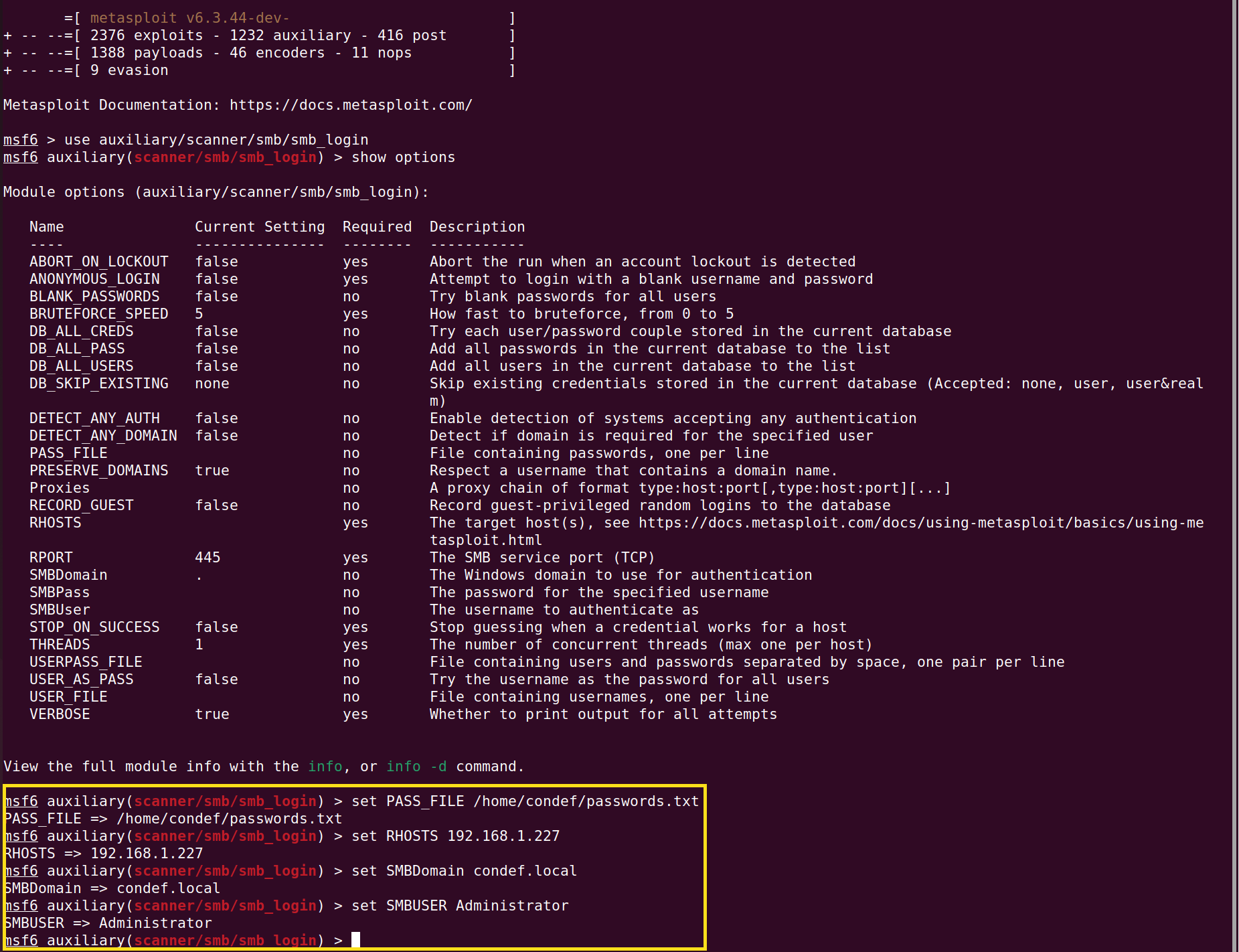
use auxiliary/scanner/smb/smb_login
Then,
set PASS_FILE /home/condef/passwords.txt where the path points to the passwords file you created in the step above
Then,
set RHOSTS 192.168.1.227 where the IP address is of your Domain Controller
Then,
set SMBDomain condef.local
Then,
set SMBUSER Administrator
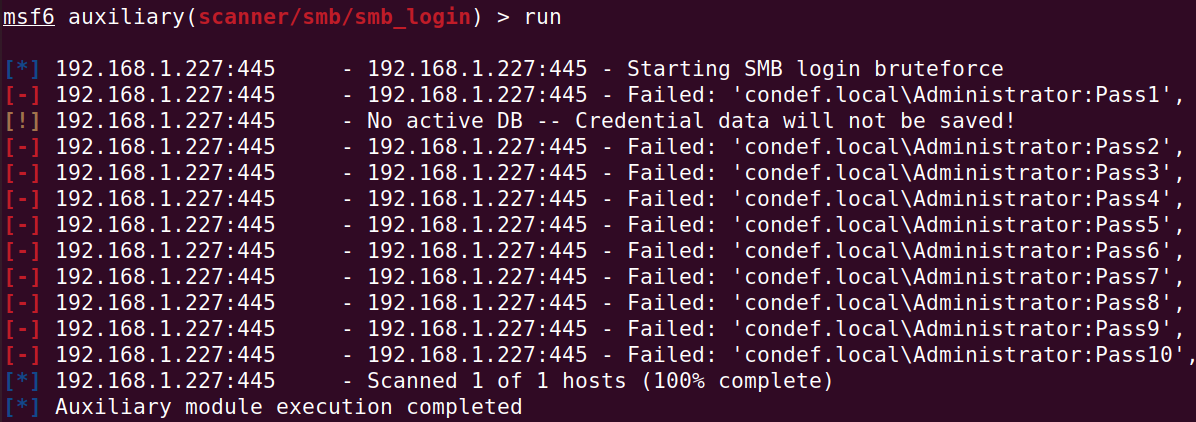
Once all your parameters are set, similar to the screenshot above, go ahead and enter in the run command and hit enter to start the brute force attempts.
You should see output similar to the below, with all the authentication attempts failing:
Now let's look at the telemetry, the event code that we want to focus on is 4625 "An account failed to log on" - let's take a look at the following query:
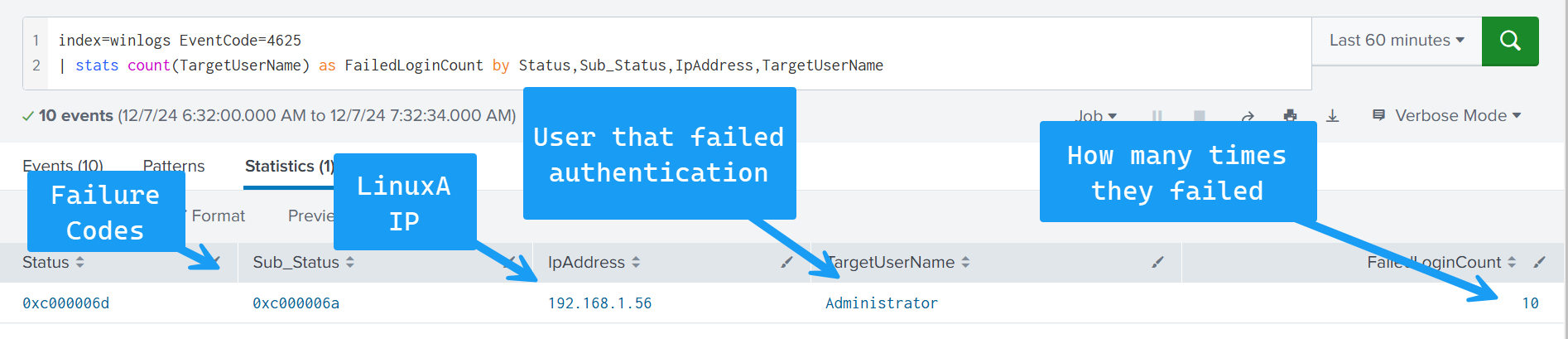
index=winlogs EventCode=4625
| stats count(TargetUserName) as FailedLoginCount by Status,Sub_Status,IpAddress,TargetUserNameThis query is:
Filtering on Event ID 4625 only
Counting how many times a target user has failed a login attempt, sorted by the status code, sub status code and source IP address
Our results will look like:
Looking at the official Microsoft documentation for this event id ( https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4625 ) - we can see exactly what the status codes mean:
0XC000006D – "This is either due to a bad username or authentication information".And
0xC000006A – "User logon with misspelled or bad password".Let's go ahead and add this translation to our query, so that we aren't looking at status codes like a computer:
index=winlogs EventCode=4625
| eval StatusTranslate = case(Status="0xc000006d","bad username or authentication information")
| eval SubStatusTranslate = case(Sub_Status="0xc000006a","User logon with misspelled or bad password")
| stats count(TargetUserName) as FailedLoginCount by Status,Sub_Status,IpAddress,TargetUserName,StatusTranslate,SubStatusTranslateAnd now our results are a little bit more readable:

At this point, we can do a couple things to make this query into a workable detection. We can either:
Broaden the time frame of the query a little bit and see if any other users have failed to login this many times in the environment
Look at the specific status codes and baseline these, and then flag on differences
These approaches are more than valid, but environments are dynamic and ever changing. You will most likely find that various accounts in the environment fail to log into systems on a regular basis.
Another approach is to use a time slice to look at authentications over time, thus making anomalies easier to spot, let's take a look at example query:
index=winlogs EventCode=4625
| bin span=1d _time
| where isnotnull(TargetUserName)
| stats count(TargetUserName) as FailedLoginCount by _time,TargetUserNameThen click on the "Visualization" tab in Splunk and select "Column Chart":

By looking at the results, we can see that there is a spike in login failures on right hand side - this method is useful for investigating brute force attacks without the need to specify an exact number of login failures, as this value will be much different depending on the environment.